Microsoft Workplace Community Blog
Windows Defender Application control - Part 1
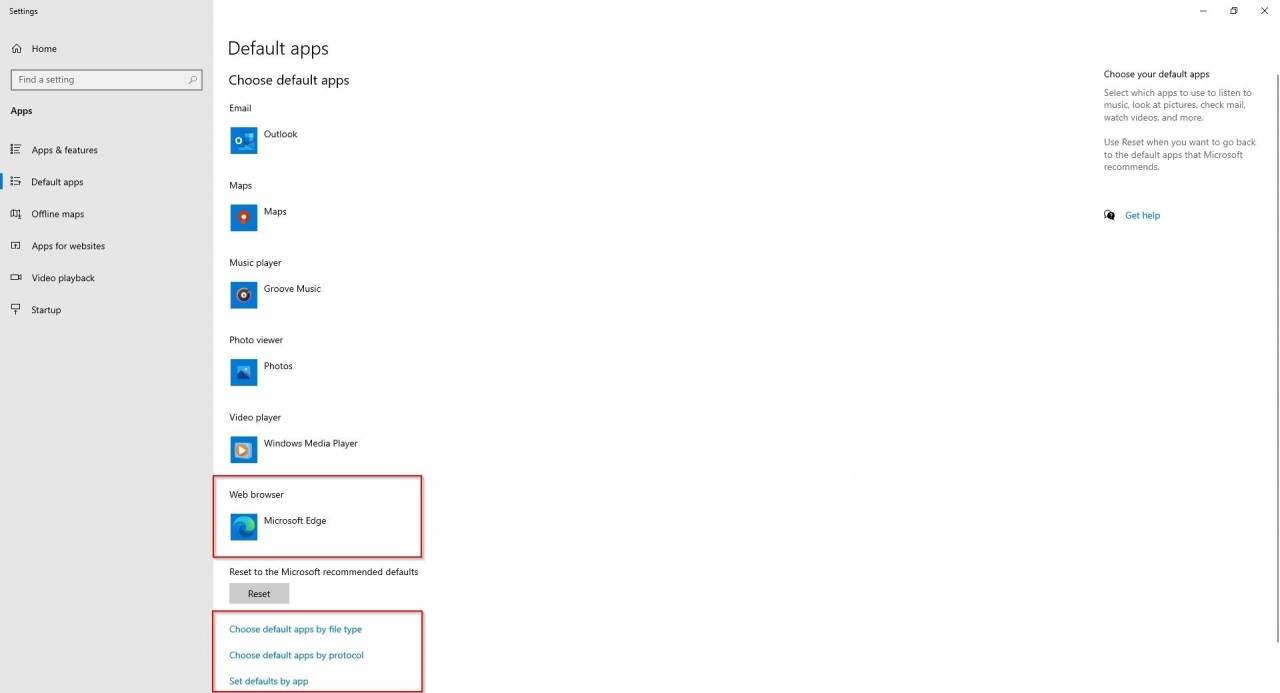
In this blog, I will explain how to implement Windows Defender Application control (WDAC) in Intune. Intune has two different ways to implement WDAC. Intune (limited built-in policies or custom policy deployment via OMA-URI). This blog will only cover the OMA-URI deployment because the built-in has no customization options and this makes the circle of trust too limited for many companies.
WDAC, like Windows AppLocker, is a way to control what is allowed to run on your Windows 10 device. The difference with AppLocker is that application control moves away from an application trust model where all applications are assumed trustworthy to one where applications must earn trust in order to run. Both applications can run side by side, but where possible Microsoft recommends using WDAC as it is a more modern approach to whitelisting and has greater security controls and enforcements.
| Application | Microsoft Defender Application Control (WDAC) |
| Weblink |
Microsoft Endpoint Manager admin center |
| Topic | Windows Defender Application Control - Intune |
In this Blog
In this blog (Part 1), I talk about how you can use Application control with Intune. After reading this blog every administrator should be able to install application control. In Part two I will talk about how you can make use of a Managed installer in Intune. This allows you to install applications from the company portal without having to define them in the WDAC policies.
| Application control Wizard | Windows Defender Application Control Wizard |
| CovertFrom- CIPolicy |
ConvertFrom-CIPolicy |
| Create Intune Configuration Profile | Microsoft Endpoint Manager |
Creating Windows Defender Application Control Policies
Windows Defender Application Control Wizard
Windows Defender Application Control Wizard
There are multiple ways to make WDAC policies. My choice is to use the Windows Defender Application Control Wizard, this wizard makes it very easy and has all the options to create a perfect policy.
- Download de application Control Wizard: Microsoft WDAC Wizard
- For more information go to the Microsoft website: Windows Defender Application Control Wizard
Create WDAC policy - Base policy
Windows Defender Application control - App
Don't use single Policy Format, this option is used by the Intune built in policy which can be found under Endpoint security.
- Launch the application, on the first screen you get three options. Since we have not created any policies yet select option "Policy Creator"
- "Multiple Policy Format" and "Base Policy" should already have been selected, if not then change this.
Create WDAC Policy - Select Base Template
Windows Defender Application control - App
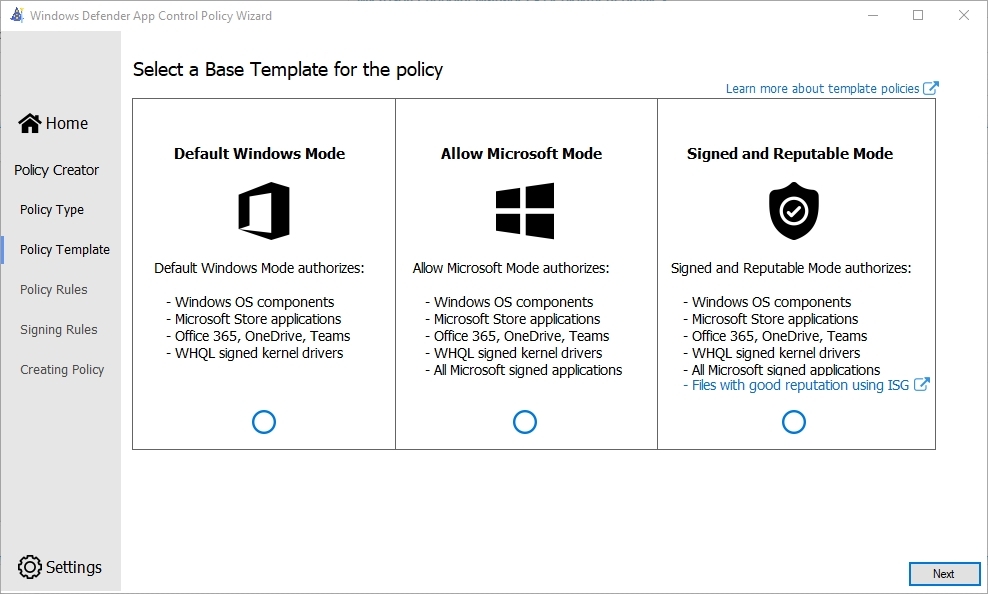
Here you have a choice of three policies. My choice here is "Allow Microsoft Mode Authorizes" since I like to trust everything from Microsoft. Microsoft itself recommends to also use "Files with good reputation ISG, but since it is impossible to find out which applications are involved, I will not use this option for now.
- Choose an option you want to use, and select Next.
Create WDAC Policy - Configure Policy Template
Windows Defender Application control - App
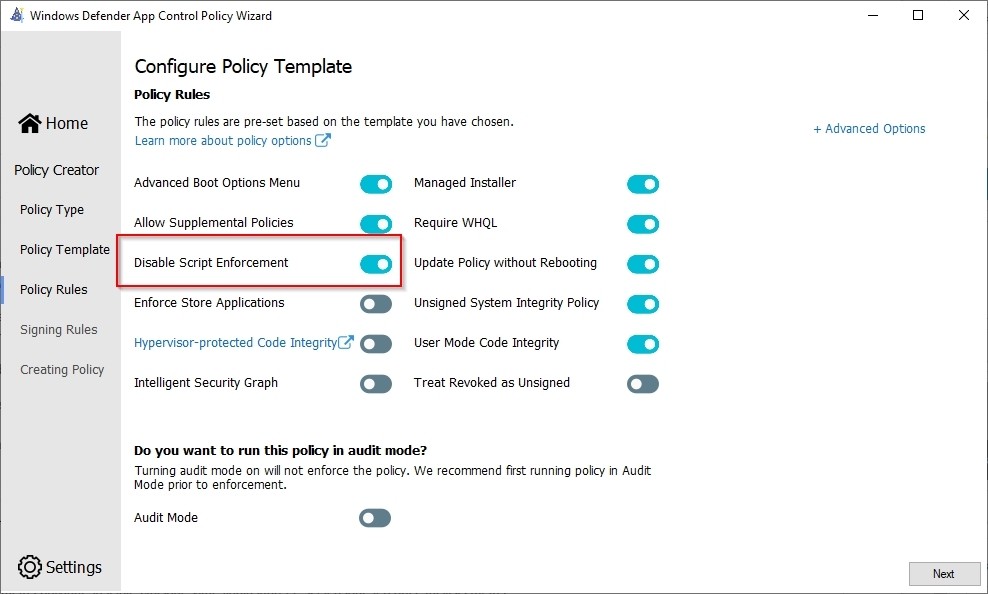
In addition to the chosen template, options can be turned on or off. Couple of these policies I will elaborate on why I turned them on or off. For a complete overview I refer you to this Microsoft website: Windows Defender Application Control - Policy Rules Description
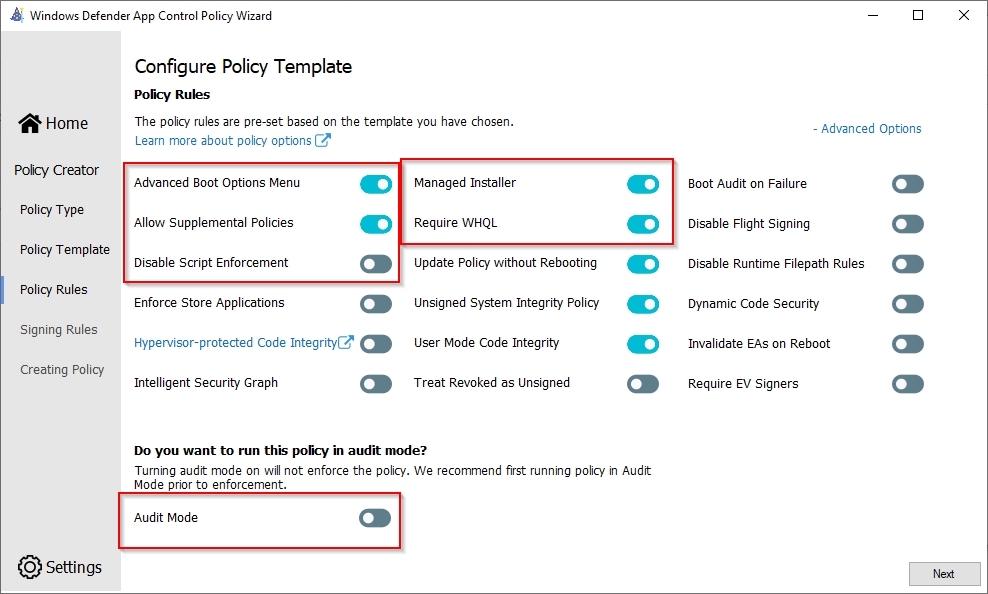
- Allow Supplemental Policies - This policy that I am making now is the basis and I will never change it. Thanks to Supplemental, I can build additional polices on top of the Base Policy.
- Disable Script Enforcement - for Part 2 I'm going to set up Intune as a managed installer and I use a PowerShell script for that, but since I don't have a certificate seining script the option must be turned on otherwise my script won't be executed.
- Managed installer - The option speaks for itself and is necessary for Part 2
- Audit mode - For production purposes it's best practice to put this in Audit modes first, but for this demo I'm obviously turning Audit modes off.
Create WDAC Policy - Policy Signing Rules
Windows Defender Application control - App
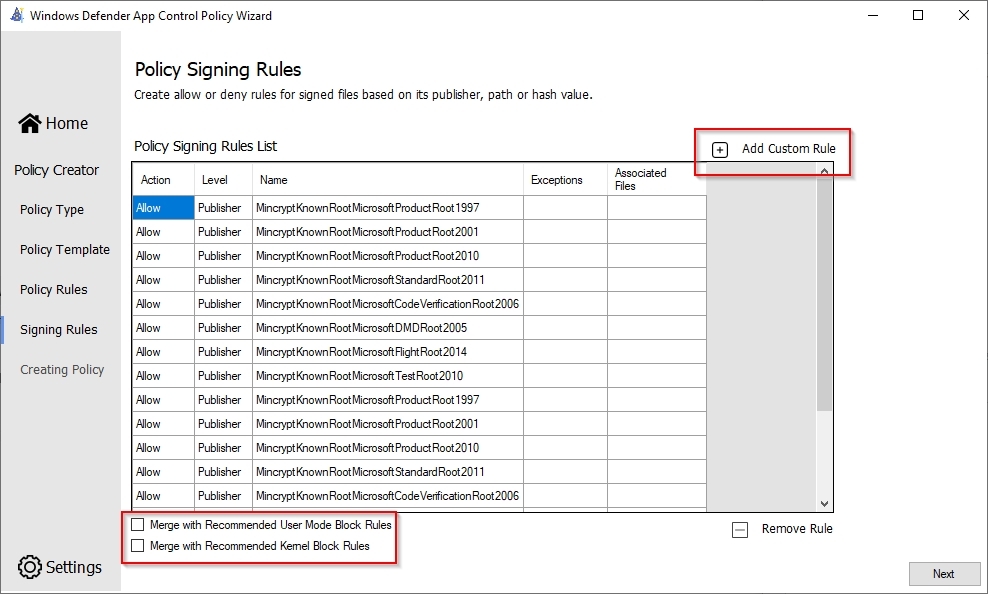
This is where you can specify all the software that you want in the Circle of Trust. I am not going to add any software here as I want to do this in part 2 with the managed installer. I do have three lines that can be added, since they are blocked by application control.
At the bottom there are also two recommendations from Microsoft, I do not include these in my base policy.
- Allow - Path Rule - Folder: C:\Program Files (x86)\Microsoft Intune Management Extension\Policies\Scripts\*
- Allow - Path Rule - Folder: C:\Program Files\WindowsPowerShell\Modules\WindowsAutoPilotIntune\5.0\*
- Allow - Path Rule - File: C:\Program Files (x86)\Microsoft Intune Management Extension\Microsoft.Management.Services.IntuneWindowsAgent.exe
- Click next to create your first WDAC base policy.
ConvertFrom-CIPolicy
Windows Defender Application control - Powershell
Since the policy is created in XML format it needs to be converted to a binary file, otherwise it cannot be used for Intune. Considering application control is an advanced ICT subject, I only give the command for converting.
Microsoft Doc: ConvertFrom-CIPolicy (ConfigCI)
ConvertFrom-CIPolicy -XmlFilePath ".\AllowMicrosoft_111621.xml" -BinaryFilePath "AllowMicrosoftPolicy01.bin"
Intune Windows Defender Application Control - Policy Import
Create Intune Configuration profiles - Custom
Windows Defender Application control - Intune
Now that we have created the policy and converted it to a .BIN file we can import it into Intune.
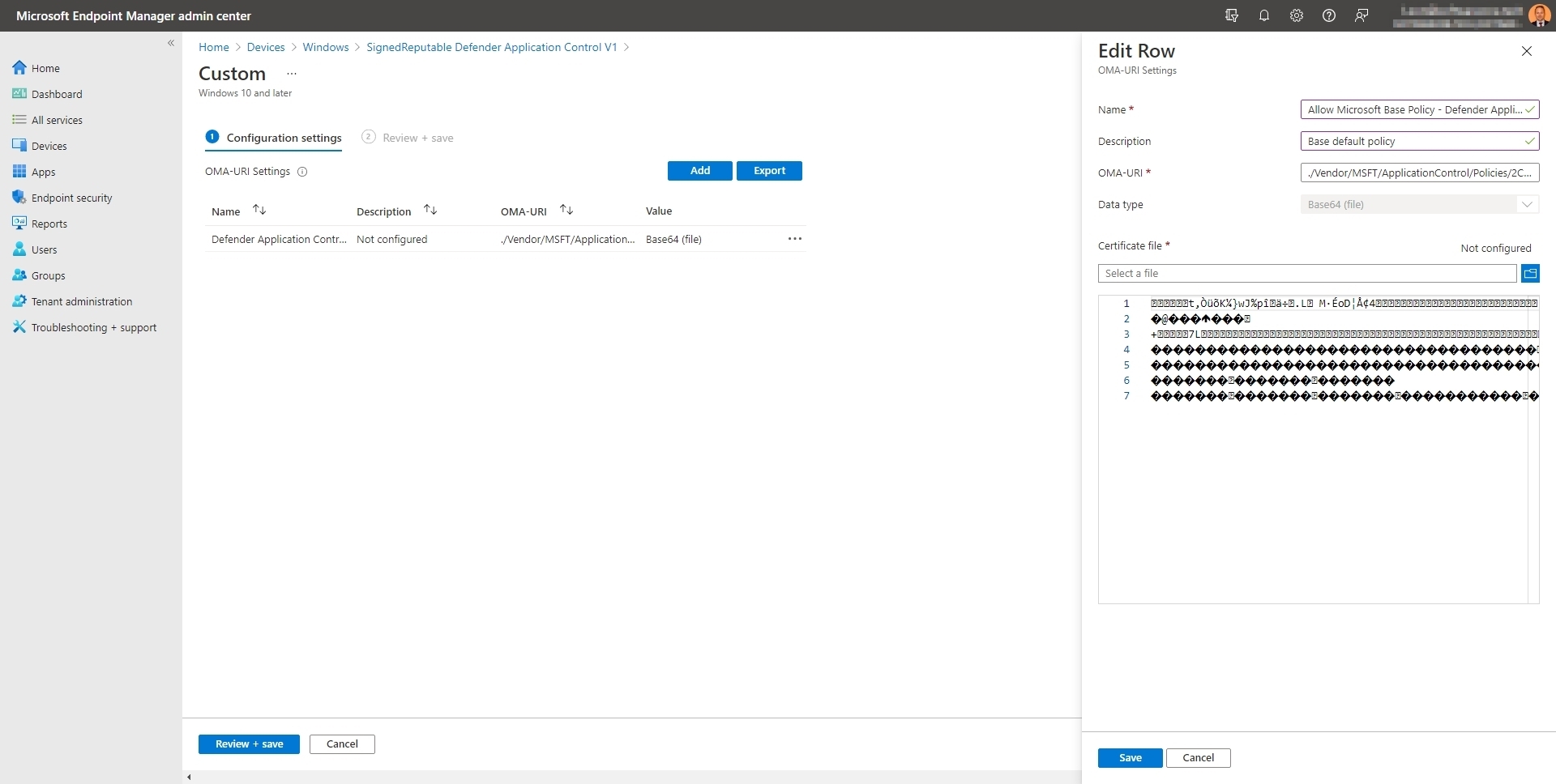
- Login to Microsoft endpoint Manager and create an "Configuration profiles - Custom"
- Name: Allow Microsoft Base Policy - Defender Application Control
- Description: Base default policy
- Know a generated policy's GUID, which can be found in the policy xml as
<PolicyID>- OMA-URI: ./Vendor/MSFT/ApplicationControl/Policies/Policy GUID/Policy
- Data Type: Base64 (file)
- Upload the create .BIN file.
See how it Looks
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.