Microsoft Workplace Community Blog
Block applications with Indicators
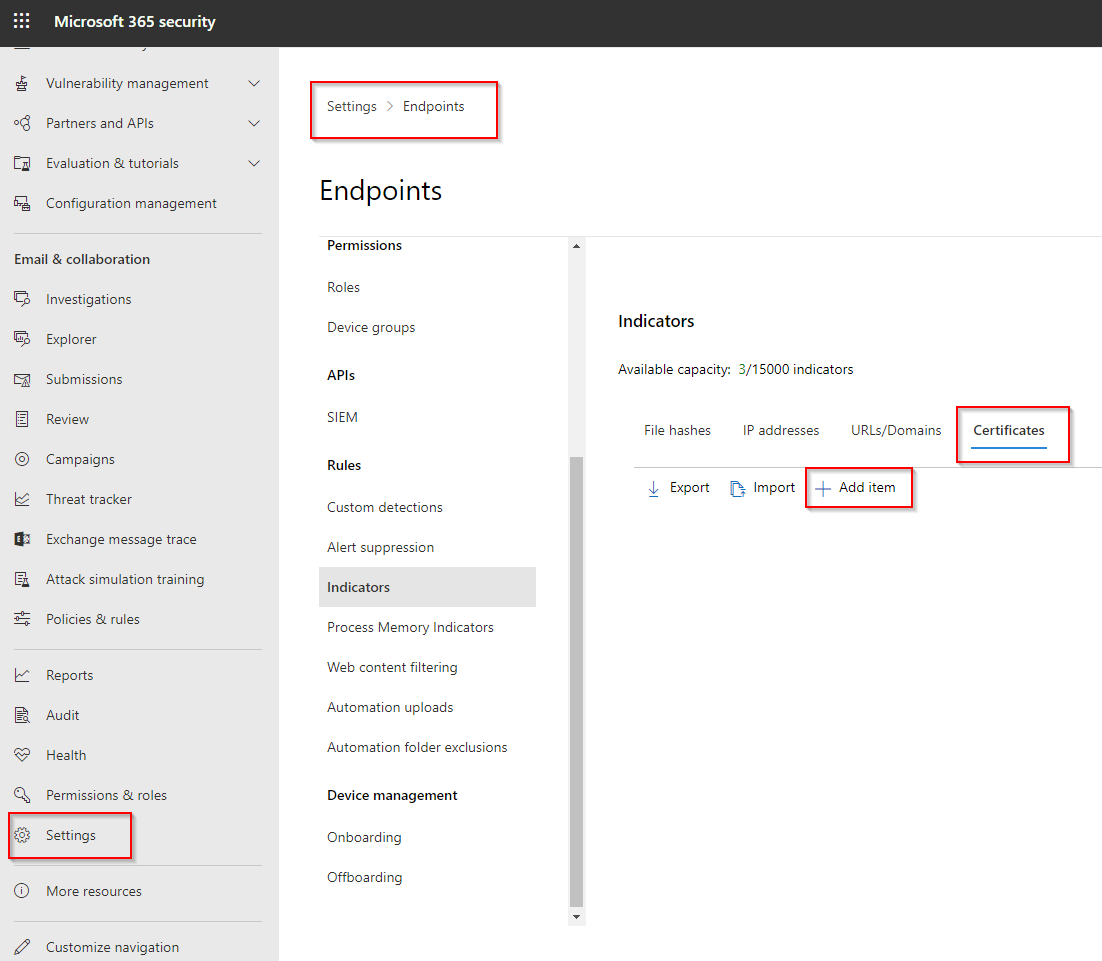
Microsoft Defender for Endpoint offers several options to block applications; you have the following options, file hashes, IP addresses, URLs/Domains and Certificates. These settings can be found at the following location in the Microsoft Defender for endpoint security portal; navigate to settings, Endpoints and under the Rules heading you will find the Indicators option.
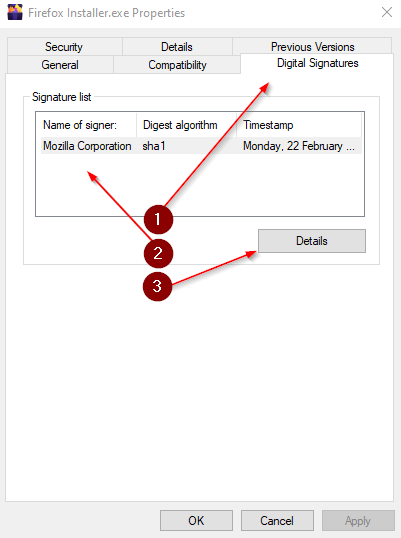
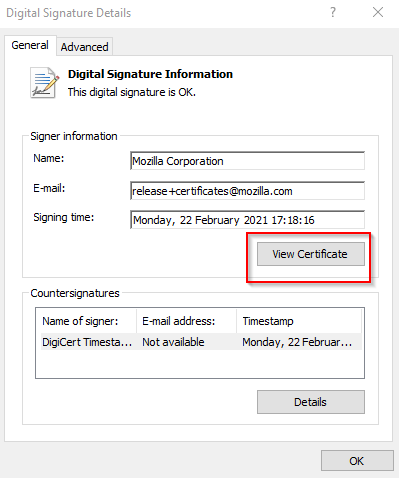
In this blog post I will explain step by step how you can use the certificate of an application to block it and also remove it if the user manage to install the application anyway. I will describe the other options in another blog later on this Year.
| Application | Microsoft Defender for Endpoint |
| Weblink |
MDATP Settings - Microsoft 365 security |
| Topic | Block Firefox application |
Steps
Below are the steps that must be taken to block an application by extracting a certificate from an executable.
| Download Firefox executable |
Download Firefox - Official website |
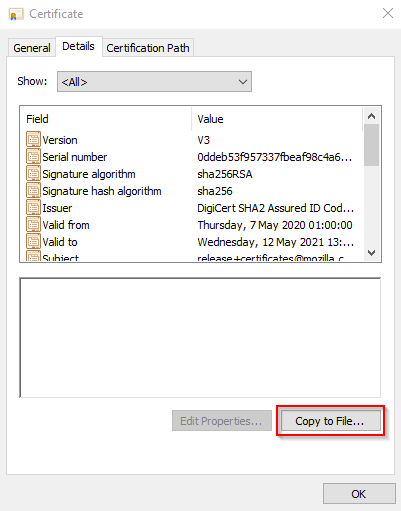
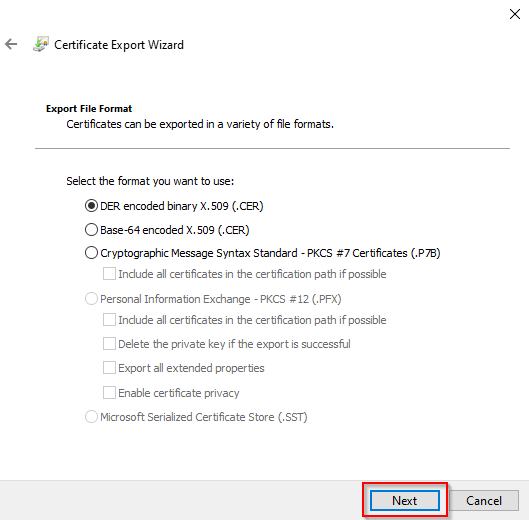
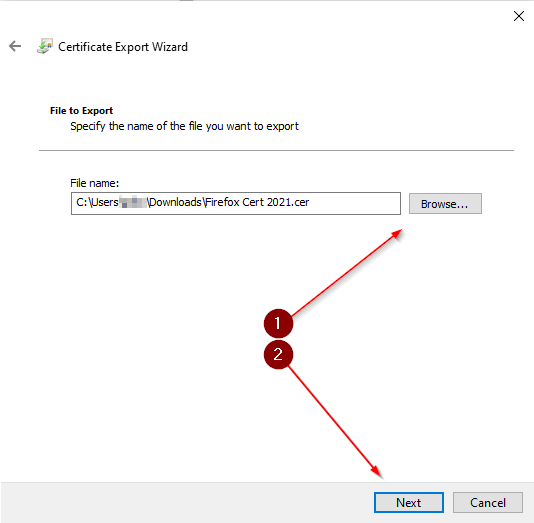
| Extract Certificate from Firefox executable |
Steps are in the Post below - Follow the steps |
| Create Policy in the Microsoft Defender for Endpoint Security Portal | MDATP Settings - Microsoft 365 security |
| Remediate devices | Steps are in the Post below - Follow the steps |
Before you begin
It's important to understand the following requirements prior to creating indicators for certificates:
- This feature is available if your organization uses Windows Defender Antivirus and Cloud-based protection is enabled.
- The Antimalware client version must be 4.18.1901.x or later.
- Supported on machines on Windows 10, version 1703 or later, Windows server 2016 and 2019.
- The virus and threat protection definitions must be up to date.
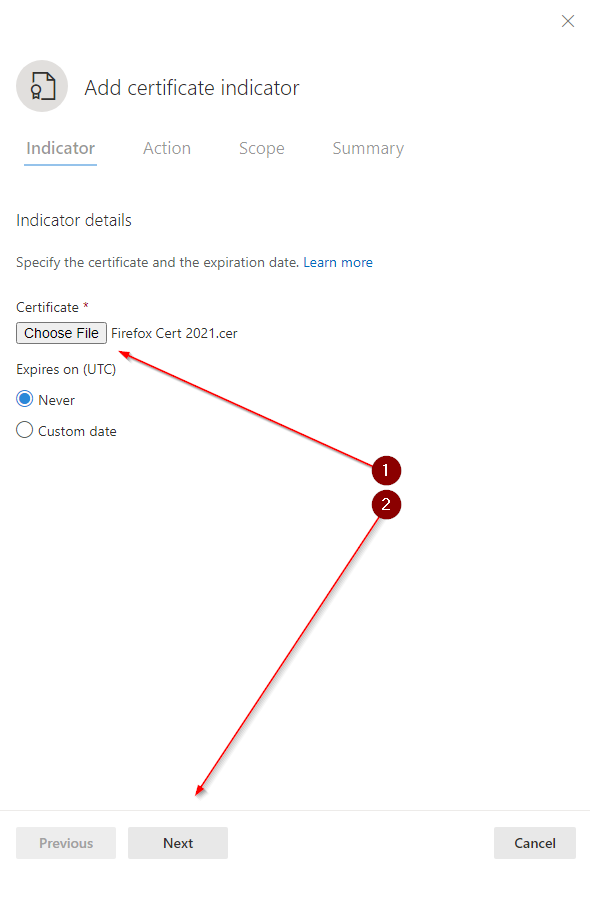
- This feature currently supports entering .CER or .PEM file extensions.
Block applications with Indicators - Block Firefox
Below I describe step by step the process to block Firefox. I am talking about Firefox, you can use any application you want. I advise you to always test it first and not to deploy directly in production.
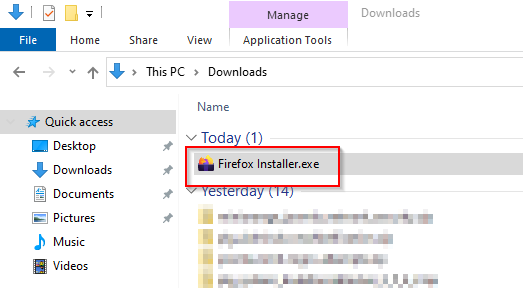
Download Firefox - Official website
The first step is to download the application. I am using Firefox as an example, but you can use any application that provides a certificate.
Navigate to the location to create the policy - Step Eight
Microsoft has announced that "SecurityCenter" is going to disappear; for that reason I show you, that the best way to create the policy is in the new "security" portal.
- Navigate to the following location "MDATP Settings - Microsoft 365 security".
- These are the steps to navigate to it.
- In the bottom left corner select "Settings".
- Then select "Endpoints".
- Then select "Indicators".
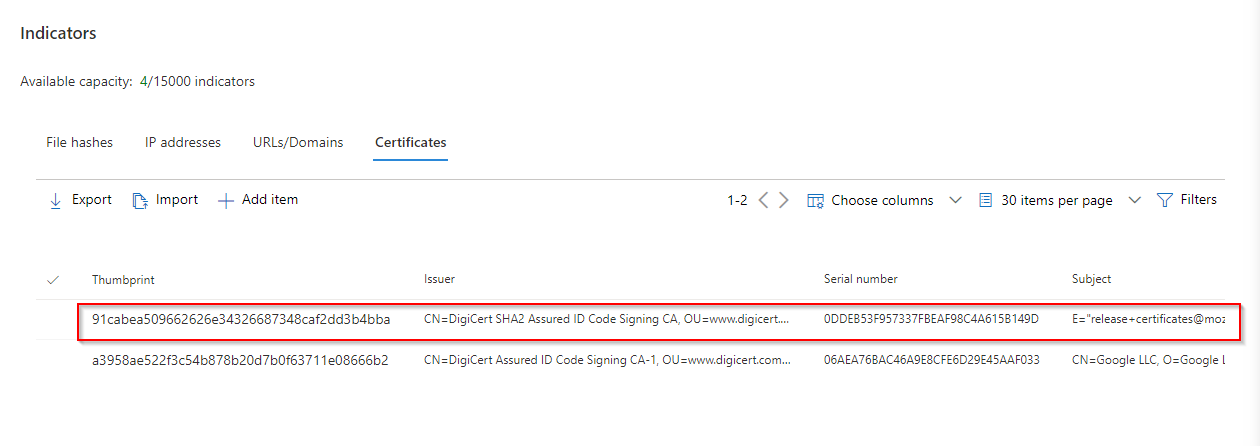
- Then select "Certificates".
- To add the certificate press "Add item".
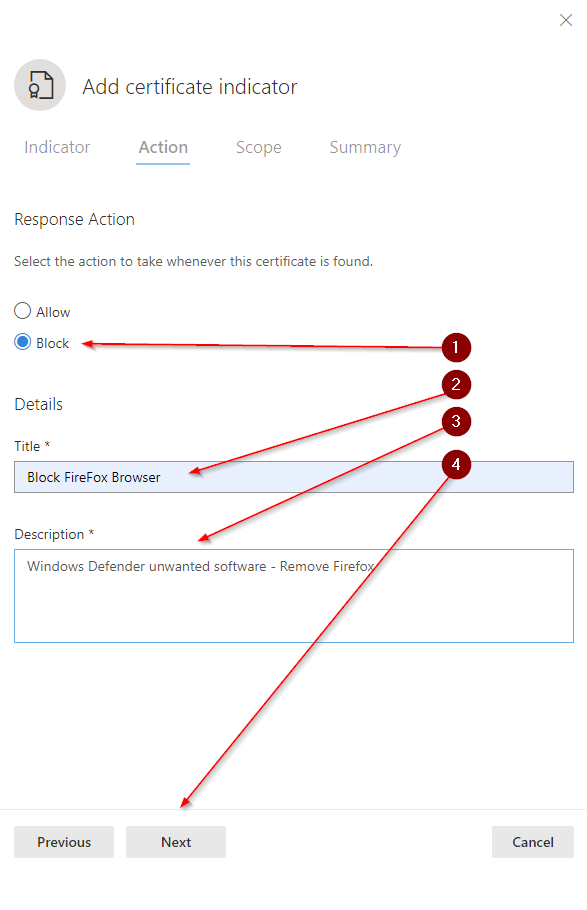
Create indicator to block Firefox - Step elevenAttention: This is an important choice. My advice is always to test new policies on a select number of devices first. So create a devices group with some test devices. I choose "all devices" since this is not a production environment but my test environment.
- So choose "select from list" here to not apply this policy to all devices immediately.
- Then click on "Next".
Below is the link to a Microsoft document how to create a device group.
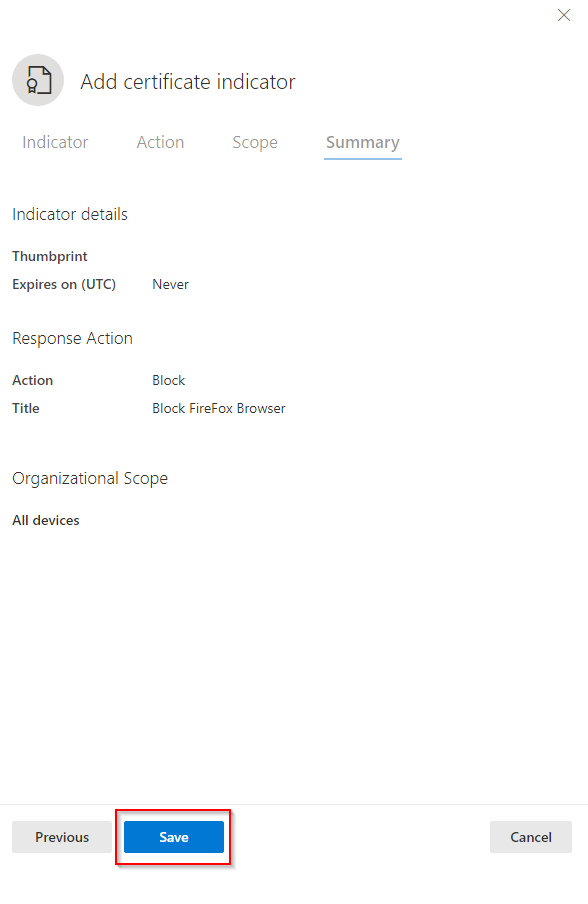
Create indicator to block Firefox - Step thirteen
This is all to create the policy. The following points are to consider.
- The time duration before this policy is active is three hours and sometimes even longer.
- Below is a demo video how quickly Windows Defender for Endpoint detects the download of Firefox. Should the user install the application anyway it will still be detected and uninstalled later, the user may then be prompted for a restart.
Create indicator to block Firefox - Step fourteen
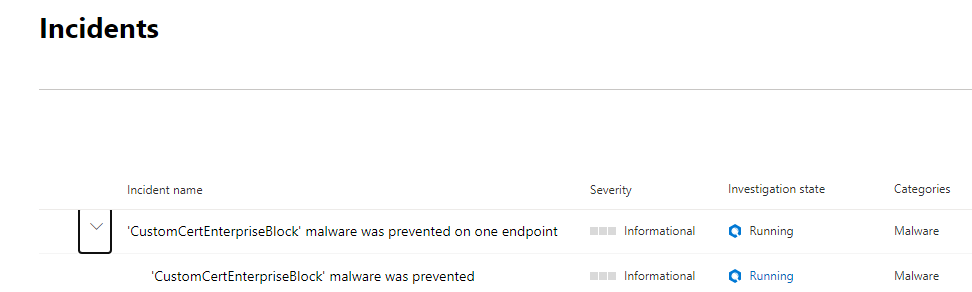
Under incidents, it indicates that there was a device that tried to install Firefox.
- Navigate to the following location "MDATP Settings - Microsoft 365 security".
- Under the section "incidents & alerts" you can view the incident
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.